The scammers getting you to buy them a mobile phone
“Hi sir. It’s Ali here, calling from O2.
This is just a courtesy call to let you know, that as a valued customer we’re willing to offer you a monthly discount of 20% on your bills. All you need to do is share your promotional code with us.
How does that sound?”
Honestly Ali, it sounds completely plausible. The patter is spot on, a standard opening gambit of any interaction between a customer and a company. The difference with this call is that Ali is a scammer and he’s reading from a carefully devised script.
If you go ahead with what Ali asks you to do next, you’ll find yourself thousands of pounds out of pocket without ever having transferred any money yourself. You probably won’t even know what happened until you realise the money has left your account.
But how?

The Scam
This particular group of scammers have discovered a distinct vulnerability in the systems we use to reset passwords online: one-time passcodes, known as OTPs. Usually four or six figure codes, these are sent at the customer’s request when we try to log in, but find that we’ve forgotten our password. OTPs offer us a way to reset the password quickly and easily.
The business will send out an OTP to the contact information associated to the account, either as an email or a text to a mobile. The customer will then get the code from their inbox, enter it into the company’s website and be able to reset their password and access their account again.
The vulnerability of course, is if the customer shares that code with anyone else. That would mean that whoever is in possession of the code can reset the customer’s password on their behalf and without their consent. If a company sends one, it’s always accompanied by a strict security message like “NEVER share this code with anyone, even our staff”.
Which takes us back to Ali. He’s employed by a group of scammers who have developed an incredibly clever ruse, tying the OTP to an imaginary promotional offer. It is intended to get you to share your code without thinking too much about the consequences.
The carrot of hugely discounted bills, at a time when most people are struggling financially, is enough to overrule your rational mind’s assessment of whether or not to share the OTP or at least to distract you from the reality of what you’re being asked to do.
The code lands in your inbox shortly after Ali has told you it will, because he’s put your number into your mobile provider’s website, and requested a password reset.
Ali will even try to offset your concerns about the security message which will accompany your code. He’ll tell you that you will indeed get a security message alongside the code, but not to worry as it’s a promotional offer, so it’s safe to share with him.
The truth is that Ali is nothing to do with O2 or any other mobile network, and is in fact sitting in an office in Lahore, Pakistan. If you share your OTP with him, he’ll immediately share it with his boss, Ahmad Sarfraz. Ahmad will then use it to reset your password, and within seconds be inside your mobile phone account online.
Whilst Ali keeps you talking, Ahmad will be using his access to your account to send all kinds of deeply private information across to Ali, like your security questions and the details of your mobile phone package.

This allows Ali to sound incredibly professional on the phone and to really convince you that he really works for your mobile phone provider. He will ask the exact security questions you’re expecting that you set up when you opened your account, like the name of your first pet, or the town you went to school in.
By giving the answers, which are then passed on to Ahmad, Ahmad is able to gain full access to your account. If your phone is tied to a contract, your payment information is already saved on the account and can be used immediately. Ahmad now has the ability to buy things using your account from the mobile phone provider’s online shop.
At this point in the call, Ali asks for a few final confirmations of your details, like your current address, and before you know it the call is over and he’s congratulating you on your newly discounted bills. He even knows exactly how much his imaginary 20% off your current bill is. He can see your details after all.
But in the background – on Ahmad’s computer in Lahore – fraud is happening. He’s buying as many expensive items as he can using your account and having them all delivered to your home address. He quickly finds the latest smartphones, tablets and accessories, whatever your mobile provider has in stock to deliver quickly and adds them to your basket, totalling thousands of pounds.
Before he does so, he’s redirecting all of your communications from your mobile phone provider to new email addresses and phone numbers he’s set up. This is so you won’t be alerted prematurely that he’s buying phones and tablets in your name.
Now the scam gets really clever. Having altered all of your contact info, Ahmad is able to receive the delivery tracking information for the new devices he’s purchased. He watches them daily on their way to your home, and on the date they’re being delivered, once he knows they’re in your possession he gives you a call.
“Hi sir. This is Ahmad calling from O2.
Unfortunately I believe there has been a mistake at our end and some devices have been delivered to you.
Would you be able to send them back to our warehouse if I send you a postage label?”
Follow Ahmad’s instructions to send the devices back to the “warehouse” and soon after he’ll be selling the phones and tablets that you paid for in one of his shops in Lahore.
The supposed warehouse is in fact one of many “mule addresses” he uses in the UK. They’re collaborators in this criminal conspiracy who are getting a percentage of the profits, in return for the use of their property.
The victims of this scam now face the nightmare of proving to their mobile phone provider that they didn’t consent to the purchase of the devices. The fact is that they no longer have the devices in their possession, so how can their mobile phone provider be sure it isn’t the customer who has sold them on and claimed fraud to be able to get a refund?
It’s an extremely difficult situation to explain and victims may well end up waiting weeks or months for the return of their money, should they get it at all.
The Scammers
Fortunately, using our ethically hacked access to their scam call centre which we obtained as part of Scam Interceptors, we were able to learn quite a lot about Ahmad Sarfraz and his Lahore-based crew.
Our breakthrough on their whereabouts came from a particularly unusual occurrence. As we sat and watched them running their scams on their computer screens, one afternoon during a long shift, Ali got hungry. Using his work computer he decided to order takeaway for the office, from a local burger joint.

The Scammers getting caught
Scammers pretending to be a phone company.
Of course, when you order a takeaway, one thing you need to do is make sure that the place you’re ordering from delivers to your location. Ali entered the full address of the office where our scammers were working as we watched his screen, allowing us to pinpoint the exact building they operated from at the time: the glamourous Madina Tower business centre, in the Muslimtown district of Lahore.

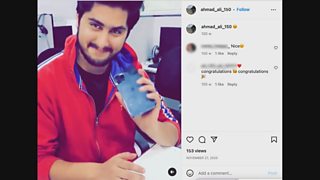
Knowing so much about these scammers also allowed us to find the boss, Ahmad Sarfraz on Instagram. His entirely open account showed a lifestyle of big spending fun – with 4x4s, fancy clothes, watches, and crucially, evidence of the actual proceeds of his crimes. He didn’t appear too concerned about getting caught.
We reported all of our evidence on Ahmad’s crew to the local police in Lahore, but unfortunately didn’t receive so much as a response. We did, thankfully, manage to catch up with Ahmad Sarfraz on the phone ourselves, when he denied all our allegations.
Our advice to avoid becoming their next victim is this: any call that comes out of the blue should be viewed as a scam until proven otherwise. Simply tell the caller that you’re going to ring back on a number you can find for the organisation they claim to represent.
One thing is for sure, if you take this step and call back anyone claiming to be your mobile provider on the genuine customer services number, you won’t be talking to Ali.

The Scammers Getting You To Buy Them A Mobile Phone
Sophisticated Scam

Watch Scam Interceptors on Monday 22nd October at 10am, 主播大秀 One, or on 主播大秀 iPlayer
